The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a law in the US published to protect privacy of patient’s medical records and health related information provided by/to patients, also known as PHI (Personal Health Information). HIPAA compliance aims to lower the administrative cost in healthcare by defining the standards in the electronic transmission of records. HIPAA is designed to help fight abuse, waste and fraud in insurance and healthcare delivery. HIPAA applies to “covered entities” and “business associates” including doctors, hospitals, health related providers, clearing houses, and health insurance providers.
Cloud computing is altering the way medics, nurses, and hospitals deliver quality, cost-effective services to their patients. It has the capacity to revolutionize healthcare, rendering it more efficiently through a decentralized approach, and improving the patient-care services and experiences. There are many secured cloud platforms like AWS, Azure, Google, IBM, etc. enabling HIPAA compliant healthcare solutions, however this blog will be focusing on AWS further. Managing HIPAA compliance in the cloud is more challenging but AWS services helps to design and implement high-load systems to process vast amounts of ePHI with HIPAA.
As AWS select partner, let us see how VOLANSYS architects HIPAA compliant cloud using AWS services.
Sign AWS Business Associate Agreement (BAA)
As per HIPAA compliance guidelines, each covered entity must follow the HIPAA security rules. AWS services are certified to ensure HIPAA compliance. AWS signs BAA agreement including legal responsibilities with customers, notifying them in case of any breach on physical infrastructure.
HIPAA compliance responsibility is on “Covered Entities” not on AWS
AWS is responsible for breach of physical infrastructure which means application level security is Covered Entities’ responsibility who are developing the application. AWS operates with shared responsibility, i.e. AWS is responsible for certain security and compliance for protecting infrastructure on AWS like Compute, Storage, Database, Network, Regions & Availability zones, Edge location.
AWS customers are responsible for services they use to create solutions,e.g. Platforms, OS, Applications, Client-Server side encryption, IAM, Network traffic protection, Customer Data.
Encryption and Protection of ePHI
Using AWS encryption services, VOLANSYS takes care of the HIPAA security rule addressing the data protection and encryption of PHI in transmission (in transit) and in storage (at rest) in cloud. AWS offers a set of features and services which provides key management and encryption of PHI.
| AWS Services for Encryption | |
| AWS KMS | KMS enables control of the encryption key which can be integrated with several services to protect data at rest and transit like S3, SQS, EBS, RDS, Elastic cache, lambda, EC2 image builder, SNS, SES and many more |
| AWS CloudHSM | CloudHSM is hardware that provides use of custom encryption keys using FIPS 140-2 level 3 validated HSM |
Auditing, Back-Ups and Disaster Recovery
Auditing and monitoring are technical safeguard which VOLANSYS addresses in architecture. This means any storage, processing or transmission of ePHI information is logged in the system to track the usage of data. The architecture will have notifications on any unauthorized access and threat on ePHI.
The solution must have an emergency plan to protect ePHI information in case of disaster to avoid the loss of patient information. It should plan the backup of collected, stored and used ePHI information with recovery processes, that can enable restoration of information in case any information is lost.
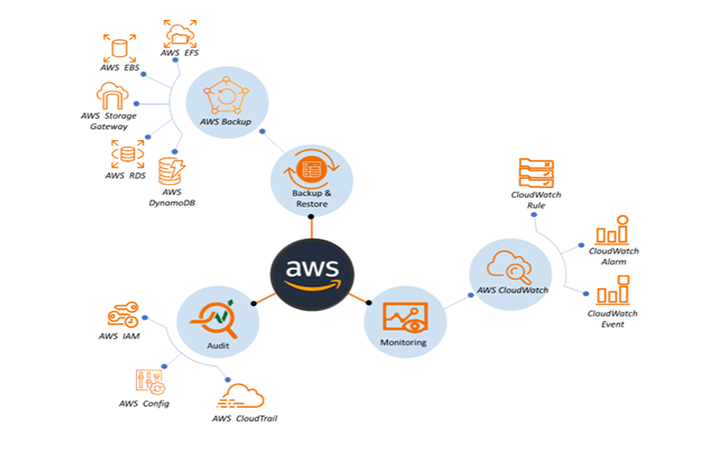
Authentication and Authorization
A HIPAA-eligible system must document the authentication and authorization mechanism in the System Security Plan with all roles and responsibilities, along with configuration control process, approvals, and process for all change requests.
Following are few points to be considered while architecting with AWS:
- IAM service to provide access to specific services
- Enable MFA to access AWS accounts
- Grant Least privileges
- Rotate credentials regularly
Architecture Strategies by VOLANSYS
One should not assume that all HIPAA eligible AWS services are secured by default, but it requires several settings to make solution HIPAA eligible. Following are few strategies which should be applied with HIPAA applications:
- Decouple the infrastructure, database and applications which are accessing/processing protected PHI data which can be achieved through,
- Turn off all public access, avoid use of access-secret keys, and use IAM with custom roles and policies and attach identity for access the services
- Enable the encryption for storage services
- Tracking the data flows and setup auto monitoring and alerts
- Keep the boundaries between protected and general workflows. Segregate the network, create external VPC with multi AZ architecture which separate subnets for different application layers and private subnets for backend application and database layers
Sample Architecture of HIPAA
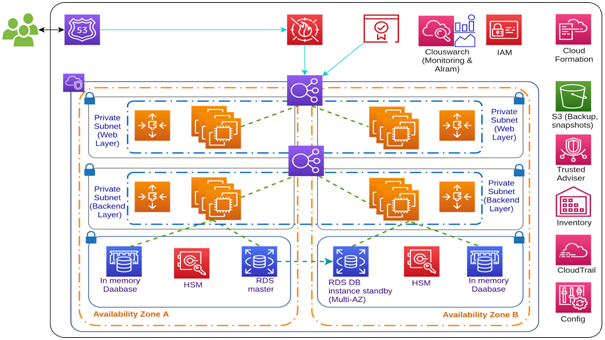
Above diagram is for 3-tier health care application which is a HIPAA eligible solution:
- Route53 is connected to WAF (Web Application Firewall) with Internal Load balancer, with this public networks are avoided, ACM (private security authority) is used to encrypt data in REST using HTTPS
- VPC (Virtual Private Cloud) is created with six private subnets in different availability zones for Web, Backend and database tier
- 2 internal ELB (Elastic Load Balancing – 1 for web and 1 for backend) with auto scaling groups to handle & distribute traffic between multiple instances and instruct to launch new instance when load is high
- MySQL and ElasticCache is launched in multiple availability zones with HSM (Hardware Security Module) to encrypt the data
- Cloudwatch is configured for monitor, setup alerts and application logs
- CloudTrail, Config and Trusted Advisor is used to audit AWS resources. IAM is used to restrict access of AWS resources and Management console
- Inventory is used to get visibility of EC2 instances
Using AWS platform, VOLANSYS can help design secure, robust, reliable, and efficient HIPAA eligible solutions. It can help you validate existing solutions to identify risks, security measures and loopholes in the system to meet HIPAA compliance requirements forany healthcare solution. Team at VOLANSYS has experience with different devices, clinical research and other healthcare companies ensuring to achieve compliance under HIPAA.

About the Author: Chandani Patel
Chandani is AWS Certified Solution Architect, AWS Business & Technical Professional, Technical Lead on several domains – Cloud Solutions, IoT Solutions, ML&Data Science. She is Cloud Solution Architect with expertise in designing, developing and architecting cloud solutions for public clouds (Azure, AWS, Google & Bluemix), private clouds & hybrid clouds.









