Internet of Things (IoT) has escalated as the most spoken issue for the past year with multiple threats rising against companies which are deploying IoT sensors and making connected devices across multiple networks subjecting themselves to further risks. Today on an average, 10 million records get lost in a day due to the breaches in the enterprise security so the possibilities of illegal access to information, unplanned surveillance through lifestyle analysis will continue to increase by 2020, as more than 50 billion devices may be connected.
- IoT Security Issues and Challenges:
The ubiquitous use of IoT technologies in wide-ranging areas have brought forth several risks, as an increased number of connected devices are giving hackers and cybercriminals more entry points. These hackers are looking for more ways to strike personal assets to critical public infrastructures, such as homes, offices, industries, traffic systems, hydroelectric dams, power grids, chemical plants, and more.
Here are some key issues and challenges faced in IoT:
- Ubiquitous Data Collection
Internet of things applications collect tons of data. Most of the connected devices store at least one piece of personal identification information like name, email, and phone and transmit this information across networks without encryption, exposing the data to vulnerability. To make life productive and comfortable, a huge amount of data is collected from the connected devices along with consumer’s private data which are fortified for future purpose.
- Poor Authentication and Authorization
If there is no way to establish the authenticity of the data being communicated to and from an IoT device, security is compromised. IoT users do not use sufficiently complex authentication credentials. A huge number of devices rely on simple to guess and effortless passwords and authorizations. This enables hackers to easily tap into legitimate user accounts and take control over IoT devices by password reset features.
- Low-Level Encryption
Data retrieval and processing is an integral part of the whole IoT environment. Most of this data is personal and needs to be protected through encryption. With everything connected, IoT smashes the defense wall and due to insufficient encryption across the network, the data are potentially infringed by cybercriminals.
- Compromised OTA (over the air) firmware update
The challenges faced in IoT is due to the offhanded attitude of the technology companies and the lazy behavior of the consumer because they do not update the devices enough or at all. The devices which were secure years back are prone to threat now; due to the advancement in the technology. Computers have been programmed with an auto-update to resolve this problem, but with the outdated hardware companies are compromising on security.
- A Proposed Secure IoT Solution Architecture using NXP A70 IC
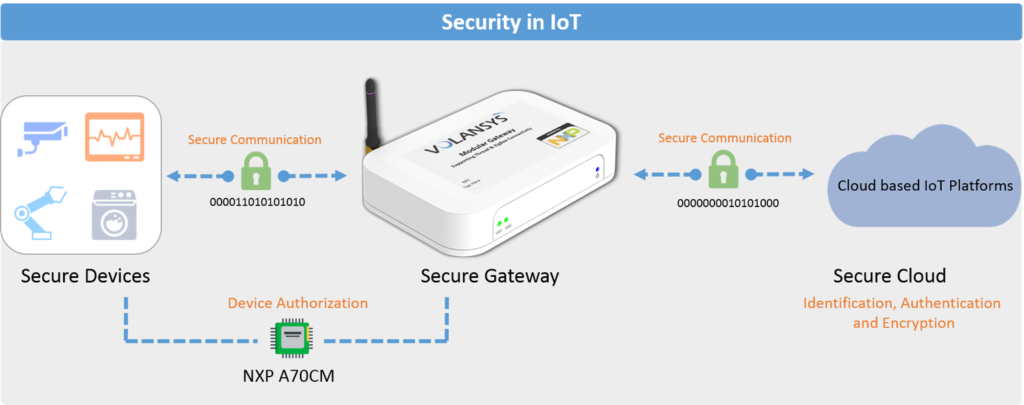
1) Secure Connected Device:
The IoT device engineers need to enforce security right from design phase by creating a platform that can protect its own integrity and which has a hardware that is strong enough to strengthen the protection. The IoT edge devices that use NXP A70 IC chip enable following key features:
- Hardware‐based key storage
- Support for widely used cryptographic standards (e.g TLS, RSA, ECC)
- End‐to‐end Secure Messaging
- Device Authentication (using PKI- asymmetric or AES – symmetric) to Cloud Apps
- Device Firmware Verification – Secure boot & OTA upgrades
2) Secure Gateway:
Many security breaches can be avoided with a robust network architecture for IoT with authentication and access control. NXP A70 IC can also be used for building a secure IoT gateway. The IC will enable gateways to be well equipped with encryption, identity management, and intrusion detection techniques to protect against the latest forms of attack and should be resilient to recover quickly in case of any damage. The A70CM can host a secret enabling the activation of gateway connected devices even in offline conditions
3) Secure Network Connections:
Some devices must exchange very sensitive messages and can’t afford to have the AES encryption key being exposed, the same key being shared among several devices for ease of deployment. The NXP A70CM IC offers several AES based encryption modes (ECB, CBC, and GCM).
Remotely extracting the key or extracting it from a few meters away using side channels (like SPA, DPA) could compromise the whole system.
The A70CM can be used to AES encrypt highly sensitive messages, the AES key never leaving the security IC which is tamper resistant. New keys can be securely loaded from a system master using key wrapping.
4) Secure Cloud Connection:
To prevent anyone from listening or accessing the data from the cloud the data that is being transferred should be encrypted. Trust must be established with a trustworthy integration of cloud compatible and it’s between the server and client before transfer. The cloud must provide with dependable data storage and segregation along with reliable cloud storage and computation for mobile devices. Key Features include:
- Make sure only approved devices connects to Cloud
- Make sure data uploaded from a device comes from that device and not from another one
- A Use Case: NXP A70CM IC for Secure Key Management
Challenges:
- The injection of keys in the supply chain is often a problem, the Electronic Manufacturing Service Provider being often untrusted or in untrusted locations
- The device manufacturer does not have a secure facility including site protection and secure servers to handle keys
- Also, the device manufacturer may want to provisionFW verification keys through another channel than the EMS building the device
Solution:
The A70CM can optionally be customized by NXP with pre‐injection of keys on behalf of customer (Trust Provisioning Service)
- Conclusion
Undoubtedly, IoT presents strong security challenges to network and security architects. Smarter and Secure IoT solutions should drive the security at each layer by including Hardware‐based key storage, end‐to‐end secure messaging, device and user authorization and authenticated cloud platform connectivity. In addition, current IoT applications need to evolve to support privacy and regulatory compliance. This article also highlights the proposed secure IoT framework with the use of NXP A70CM IC for applying security right from hardware layer. More intelligent security frameworks that incorporate threat detection, anomaly detection and predictive analysis need to advance.
- How VOLANSYS Can Help in Providing Security In IoT
VOLANSYS have years of expertise in providing services & solutions for IoT in all industries & domains, including healthcare, smart appliances for home & office, Industrial IoT (IIoT), smart consumer devices, and others. With the escalated concern regarding security in IoT, we have developed an array of solutions that facilitates our customers to profit by integrating the right level of security in the connected devices without compromising on the user experience.
To know more regarding the security solutions mail us on [email protected] or call us at +1 510 358 4310.









